

Sensitive data is all around us!
Applications can store various types of data depending on their purpose and functionality. In many cases the data stored by application can be considered sensitive. If this kind of data is compromised (meaning a malicious party has gained unauthorized access to this data) it could lead to significant harm to an individual or an organization. Therefore it is paramount that this kind of data is protected in any way possible.
Protecting sensitive data
There are many ways of protecting data within applications. The most common ways are:
Access Controls: Applications can protect sensitive data by implementing access controls, such as user authentication and authorization. This ensures that only authorized users can access the data, and that access is restricted based on their role or permission level.
Data Backups: Regular data backups ensure that even if data is lost or compromised, it can be restored quickly without significant loss. Data backups can also be stored in a secure location, away from the primary database to ensure that in case of a disaster, data can still be recovered.
Encryption in transit: One of the most effective ways to protect sensitive data is by encrypting it. Encryption in transit is a security measure that involves encrypting data as it travels between two endpoints, such as a client and server or between two servers, to protect it from unauthorized access or interception. Encryption in transit typically involves using protocols such as HTTPS, TLS, and SSL to establish a secure connection between the client and server. These protocols use encryption algorithms to encode the data being transmitted so that it can only be read by the intended recipient. Encryption in transit also involves digital certificates that validate the identity of the server and ensure that the data is being sent to the correct recipient.
- Encryption at rest: a security measure that involves encrypting data when it is stored on a device, such as a hard drive or a database, to protect it from unauthorized access or theft. When data is at rest, it is vulnerable to theft or unauthorized access from physical access or a cyber attack. Encryption at rest helps to mitigate these risks by rendering the data unreadable without the correct encryption key, even if an attacker gains physical or remote access to the device where the data is stored.
NoCode-X offers encryption at rest without the hassle!
Start building your Application website automatic process
Encryption at rest has never been this easy to implement… seriously! NoCode-X offers it out of the box based on a data classification system. It works as follows:
Each part of data within applications built with NoCode-X can be classified. Each classification has its own set of measures that is automatically enforced on the data labelled with this classification. One of those measures is encryption at rest! In short: All data labeled as “secret”, “medical” or “restricted” is automatically encrypted at rest.
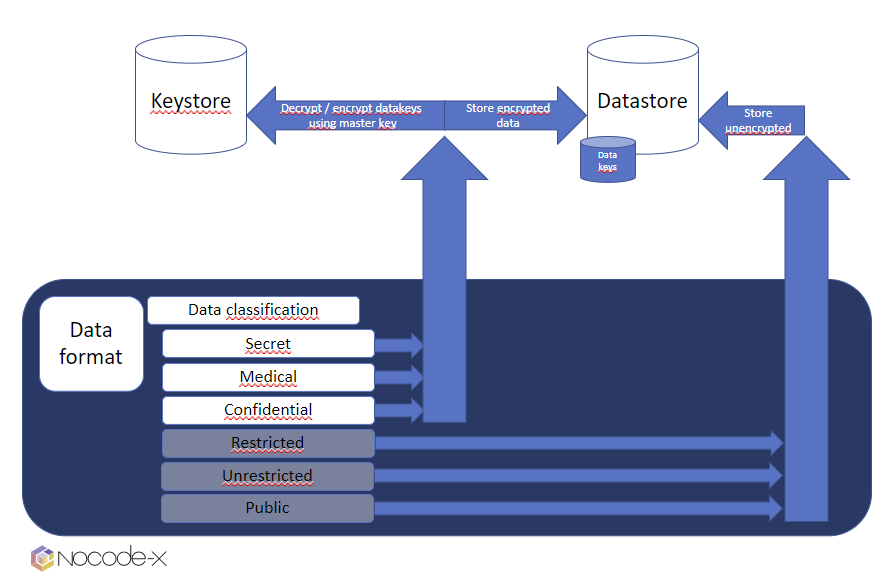
We encrypt your data with the utmost care. Technically, it boils down to this: We keep a master key for your application within a secure keystore. This masterkey never ever leaves this keystore and is used to encrypt/decrypt datakeys. These datakeys are used to encrypt / decrypt your data.
We’ve designed it specifically for 2 reasons:
- masterkey, datakeys & data are all being stored in different datastores, which means a malicious party needs at least access to all three stores before data is compromised.
- Thanks to this architecture, we can regularly rollout new versions of the masterkey & subsequently replace old datakeys with newer versions. Meaning a higher level of security. Compare it with a password that you change every week which is much harder to hack compared to a password that never changes.
We can build your Internal application Highly secure automation Customer facing app
Subscribe to our newsletter
Interested in all updates to our platform? Subscribe to our newsletter.
